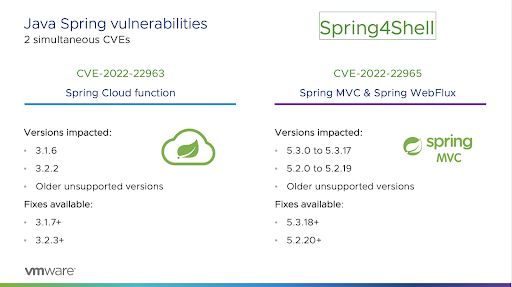
Spring Bean is a powerful dependency injection framework used in Java applications. It simplifies the process of creating and managing objects within an application by allowing developers to define beans (objects) and their dependencies in a configuration file. However, like any software, Spring Bean can be vulnerable to security issues.
Types of Spring Bean Vulnerabilities
There are several types of vulnerabilities that can affect Spring Bean, including:
Remote Code Execution (RCE): This vulnerability allows an attacker to execute arbitrary code on the target system by exploiting a flaw in the Spring Bean configuration or code.
SQL Injection: This vulnerability allows an attacker to execute arbitrary SQL queries on the target system by exploiting a flaw in the Spring Bean configuration or code that handles SQL queries.
Cross-SiteScripting (XSS): This vulnerability allows an attacker to inject malicious JavaScript code into the target system by exploiting a flaw in the Spring Bean configuration or code that handles user input.
Denial of Service (DoS): This vulnerability allows an attacker to prevent the target system from responding to legitimate requests by exploiting a flaw in the Spring Bean configuration or code.
Causes of Spring Bean Vulnerabilities
Spring Bean vulnerabilities can be caused by various factors, including:
Misconfiguration: Improper configuration of Spring Bean can lead to vulnerabilities. For example, if a bean is exposed to remote access without proper security measures, it can be exploited by attackers.
Code Flaws: Vulnerabilities can also be introduced due to flaws in the implementation of Spring Bean itself. These flaws can allow attackers to bypass security controls or exploit the framework in unexpected ways.
Third-Party Dependencies: Spring Bean relies on various third-party libraries and frameworks. Vulnerabilities in these dependencies can also affect Spring Bean applications.
Mitigation Strategies
To mitigate Spring Bean vulnerabilities, it is crucial to follow best practices such as:
Use Secure Configurations: Configure Spring Bean securely by limiting remote access to beans, using strong passwords, and implementing appropriate access controls.
Keep Software Up-to-Date: Regularly update Spring Bean and its dependencies to patch any known vulnerabilities.
Validate User Input: Sanitize and validate user input to prevent malicious inputs from being exploited.
Implement Security Controls: Implement security controls such as firewalls, intrusion detection systems, and web application firewalls to protect the system from attacks.
Monitor and Audit: Regularly monitor and audit Spring Bean applications to detect and respond to potential vulnerabilities.
Conclusion
Spring Bean is a powerful tool for developing Java applications, but it is not immune to vulnerabilities. By understanding the types of vulnerabilities, their causes, and mitigation strategies, developers can implement secure Spring Bean applications that are less susceptible to attacks. Regular security assessments and updates are crucial to maintain the security of Spring Bean applications in a constantly evolving threat landscape.
[model: toolbaz_v2]
Tags: Cybersecurity
Spring-Bean