A CVE Number (Common Vulnerabilities and Exposures number) is a unique identifier assigned to a specific cybersecurity vulnerability. The CVE system is designed to provide a standardized way of identifying and cataloging vulnerabilities across various software, hardware, and firmware systems, allowing security professionals to easily reference and discuss specific issues.
### Key Points About CVE Numbers:
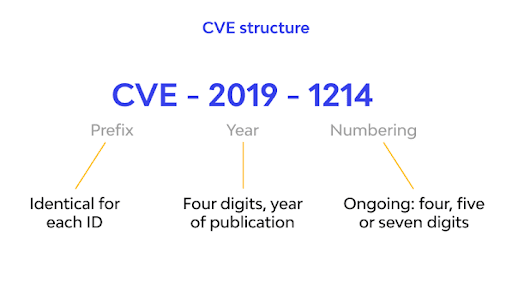
1. **Structure of a CVE Number**:
- A CVE number follows the format `CVE-YYYY-NNNN`, where:
- `YYYY` is the year the vulnerability was publicly disclosed.
- `NNNN` is a unique identifier for the vulnerability within that year (e.g., `CVE-2023-12345`).
- As the number of vulnerabilities has grown, the format allows for flexibility, such as adding additional digits (e.g., `CVE-YYYY-NNNNNN`) if necessary.
2. **Purpose**:
- CVE numbers provide a common identifier for known vulnerabilities, helping security teams, vendors, and researchers reference the same issue consistently.
- By using a CVE number, security updates, patches, and reports can clearly communicate which specific vulnerabilities they address.
3. **CVE List**:
- The CVE List is maintained by the **MITRE Corporation** and is part of the National Cybersecurity Federally Funded Research and Development Center (NCF), operated by MITRE. It contains entries for publicly known vulnerabilities in widely used software and hardware.
- The CVE List is used by various vulnerability databases, such as the National Vulnerability Database (NVD), to provide detailed information about vulnerabilities.
4. **How CVE Numbers Are Assigned**:
- Vulnerabilities are assigned CVE numbers by **CVE Numbering Authorities (CNAs)**, which are organizations authorized to assign CVE identifiers for specific products or regions.
- Examples of CNAs include major software vendors like Microsoft, Oracle, and Google, as well as cybersecurity organizations.
5. **Using a CVE Number**:
- When a vulnerability is identified, security bulletins, patches, and advisories will often reference its CVE number. This allows security professionals to track the status of that vulnerability and determine if it has been patched or if it is actively being exploited.
### Example:
- **CVE-2023-12345**: This might represent a specific buffer overflow vulnerability discovered in a popular software product in 2023. The CVE entry will contain details about the nature of the vulnerability, affected systems, and potentially how to mitigate it.
In summary, CVE numbers are crucial for the standardized tracking and management of cybersecurity vulnerabilities, enabling organizations to coordinate responses to security threats effectively.