The threat hunting process is an iterative, proactive methodology used by cybersecurity teams to search for hidden threats that have evaded automated detection tools. It assumes breaches may already be present and relies on human expertise, threat intelligence, and data analysis to uncover them. Unlike reactive incident response, threat hunting is hypothesis-driven and continuous, aiming to reduce attacker dwell time.
A widely referenced model is the Threat Hunting Loop (originally from Sqrrl, now foundational in the industry), which consists of four core stages. Other frameworks, such as those from CrowdStrike and Fortinet, simplify it into three phases (Trigger, Investigation, Resolution), while more detailed ones expand to include planning and reporting.
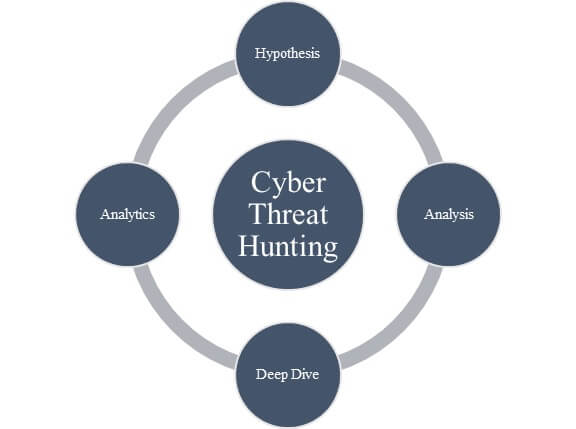
Common Stages of the Threat Hunting Process
Here's a breakdown of the typical steps, drawing from established models like the Threat Hunting Loop and MITRE ATT&CK-guided hunting:
- Hypothesis Formation (or Trigger/Planning) Start with a lead or "trailhead": Form a testable hypothesis based on threat intelligence (e.g., MITRE ATT&CK TTPs), anomalies, recent attacks, or risk assessments. Examples: "Attackers may be using PowerShell for lateral movement" or "Endpoints accessed from unusual locations could indicate compromise." Define scope, objectives, and expected outcomes.
- Investigation (or Execution/Data Collection & Analysis) Collect and query data from sources like endpoints (EDR logs), networks (packet captures), SIEM systems, authentication logs, and threat intelligence platforms. Analyze for indicators of compromise (IOCs), indicators of attack (IoAs), anomalies, or adversary behaviors. Use tools for querying, visualization, and behavioral analytics.
- Resolution (or Uncover/Disrupt) Validate findings: Confirm if the activity is malicious, benign, or a false positive. If a threat is identified, remediate (e.g., isolate hosts, block IPs) and contain the incident. Document evidence for incident response.
- Improvement (or Automation/Feedback Loop) Enrich defenses: Turn validated findings into new detection rules, signatures, or automated analytics. Generate new intelligence (e.g., update baselines of normal behavior) and refine future hypotheses. This closes the loop, making the process iterative.
The process is often visualized as a cycle to emphasize continuity.
- Iterative and Proactive: Hunts are repeated regularly, with learnings feeding back into tools and intelligence.
- Human-Led with Tool Support: Combines analyst creativity with SIEM, EDR, UEBA, and machine learning.
- Types of Hunts: Hypothesis-driven (most common), intelligence-driven (based on known IOCs/TTPs), or data-driven (anomaly detection via baselines).
- Integration with Frameworks: Often aligned with MITRE ATT&CK for structuring hypotheses around adversary tactics and techniques.
Effective threat hunting requires skilled analysts, quality data, and maturity progression (e.g., via the Hunting Maturity Model from HM0: reactive only, to HM4: advanced, automated hunts). It complements automated detection and significantly improves an organization's security posture by uncovering stealthy threats early.
