The
websites you visit every day represent just a small fraction of the whole
internet. Beyond this “surface web” is the deep web, and within the deep web is
the dark web.
Surface web is the normal web which is visible for all users using internet. The websites in the surface web is indexed by search engines. Google is the great example of search engine. The user can open websites and gain information. But the interesting thing is that the surface web is only a 4% area of internet that the users used. The internet is a bigger place.
The surface web is also called as Lightnet or Indexed Web
What is the Deep Web: Deep web is the secret web which is not visible for normal user. The deep web consist of a website or any page on the website which are not indexed by search engines. The user can only access it if he/she has a authorized person to access it and has any permission like (Url, username and password etc). Deep web is used to store most personal information like (Cloud storages, any organization personal data and military data etc).
The Deep web is also called as Hidden Web or invisible Web
What is the Dark Web?
Now we can discuss about the most dangerous part of the internet which is called dark web or darknet. Dark Web is illegal to used. The all criminal activities are act upon on dark web. The criminal activities like drugs dealing, killing humans etc. The user can only access it if the user has Tor Browser. The Tor means The Onion Router. It can make a layers of many IPs and the user surf the internet anonymously. Many dark web websites are banned by Tor but the dark web is totally not cleared.
The writing of this article is only for knowledge. I don’t promote illegal activities and I am not responsible for any illegal activity.
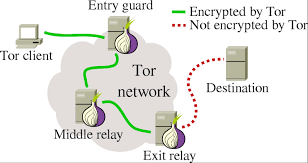
The TOR Browser: The TOR browser is a web browser that anonymize your web traffic using the TOR network, Making it easy to protect your identity online.
The Tor project is a non-profit organization that conducts research and development into online privacy and anonymity. It is designed to stop people – including government agencies and corporations – learning your location or tracking your browsing habits.
Based on that research, it offers a technology
that bounces internet users' and websites' traffic through "relays"
run by thousands of volunteers around the world, making it extremely hard for
anyone to identify the source of the information or the location of the user.
Its software package – the Tor browser bundle –
can be downloaded and used to take advantage of that technology, with a
separate version available for Android smartphones.
There are some trade-offs to make: for example,
browsing using Tor is slower due to those relays, and it blocks some browser
plugins like Flash and QuickTime. YouTube videos don't play by default either,
although you can use the "opt-in trial" of YouTube's HTML5 site to
bring them back.
Who created Tor?
The original technology behind Tor was
developed by the US navy and has received about 60% of its funding from the
State Department and Department of Defense, although its other backers have
included digital rights lobbyist the Electronic Frontier Foundation, journalism
and community body Knight Foundation and the Swedish International Development
Cooperation Agency.
When it launched in 2002, the Tor project's
emphasis was on protecting internet users' privacy from corporations rather
than governments.
"We were increasingly concerned about all
these websites - in the 2000/01 dotcom bubble, everyone was offering free
services, and by free they meant 'we take all your information and sell it as
many times as possible'," executive director Andrew Lewman told the Guardian
in April 2012.
Who uses Tor?
The Tor project team say its users fall into
four main groups:
Normal people who want to keep their internet
activities private from websites and advertisers; those concerned about
cyberspying; and users evading censorship in certain parts of the world.
Military professionals the US navy is still a
key user.
Journalists- they are using for information gathering
and information sending.
The Tor is also used by business executives, IT professionals and law enforcement officers as key users, with the latter including police needing to mask their IP addresses when working undercover online, or investigating "questionable web sites and services".


Nice post
ReplyDelete