Graphics Processing Units (GPUs) from NVIDIA, AMD, Intel, and ARM are powerhouse components ideal for parallel computing tasks. This makes them prime targets for hackers: cryptomining (cryptojacking) leverages their efficiency to mine cryptocurrencies stealthily, while espionage uses subtle side-channel leaks to spy on sensitive data or applications. GPU drivers—software bridging the OS and hardware—are often the weak link, vulnerable to exploits, malware injection, or architectural leaks.
As of late 2025, vulnerabilities in GPU drivers continue to emerge (e.g., NVIDIA's frequent bulletins fixing privilege escalation and buffer overflows), enabling everything from resource theft to advanced persistent threats.
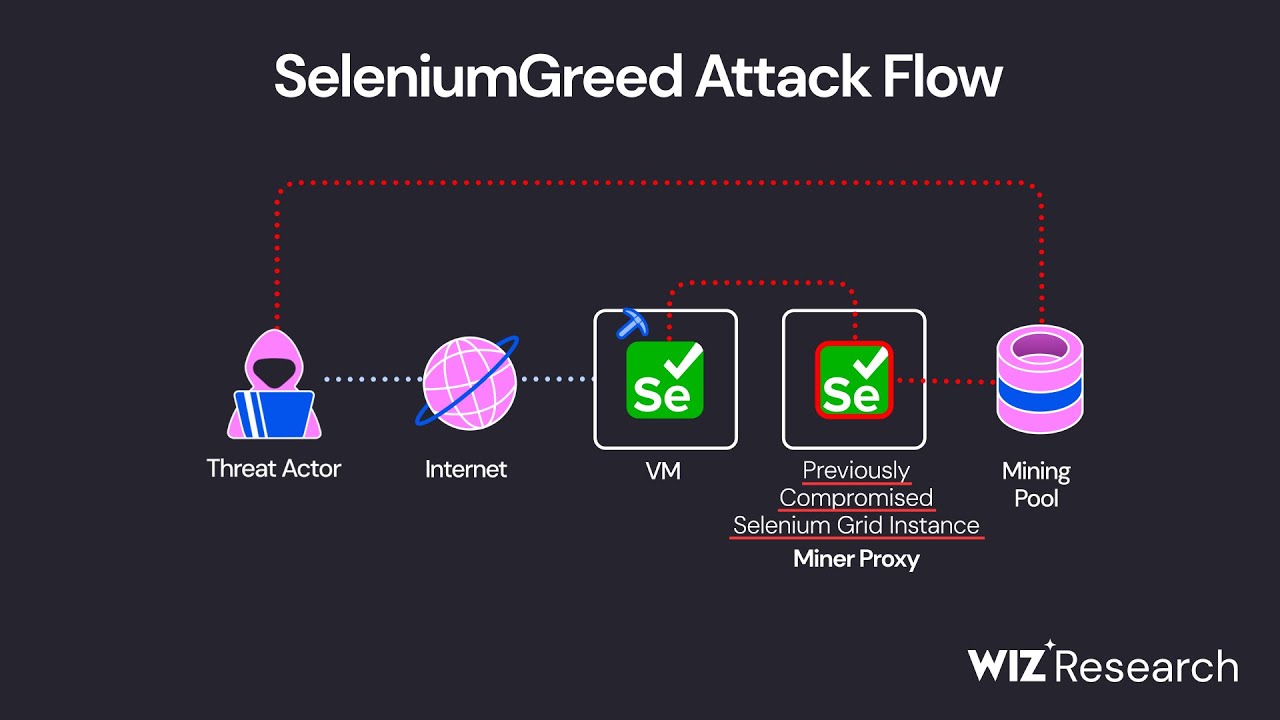
Illustration of cryptojacking malware hijacking GPU resources.
Cryptomining Exploitation: Turning Your GPU into a Money Printer
Hackers love GPUs for mining coins like Ethereum Classic or Monero because they outperform CPUs by orders of magnitude in hash calculations.
Common Techniques:
- Initial Access via Driver Vulnerabilities: Attackers exploit flaws in GPU drivers for privilege escalation or code execution. For example, NVIDIA has patched multiple high-severity issues in 2024-2025 allowing local attackers to gain kernel-level access, which can then install mining malware. ARM Mali drivers have seen use-after-free bugs leading to full device compromise on Android.
- Malware Delivery:
- Fake "mining optimizers" or LHR (Lite Hash Rate) bypass tools for NVIDIA cards, often packed with trojans (e.g., 2022 incidents where tools promising to unlock mining limits were malware-laden).
- Bundled in pirated software targeting designers/architects (e.g., cracked Adobe or Autodesk installers embedding PhoenixMiner or lolMiner).
- Drive-by cryptojacking via browser scripts (Coinhive-style, though less common now) or compromised cloud instances.
- GPU-Specific Loaders: Advanced malware like CoffeeLoader (2025) uses the GPU itself for unpacking payloads, evading CPU-based detection. Teams like TeamTNT install legitimate NVIDIA drivers on compromised servers to enable efficient mining.
- Outcome: Silent GPU overuse drains power, heats hardware, and racks up electricity bills—while profits go to the attacker.

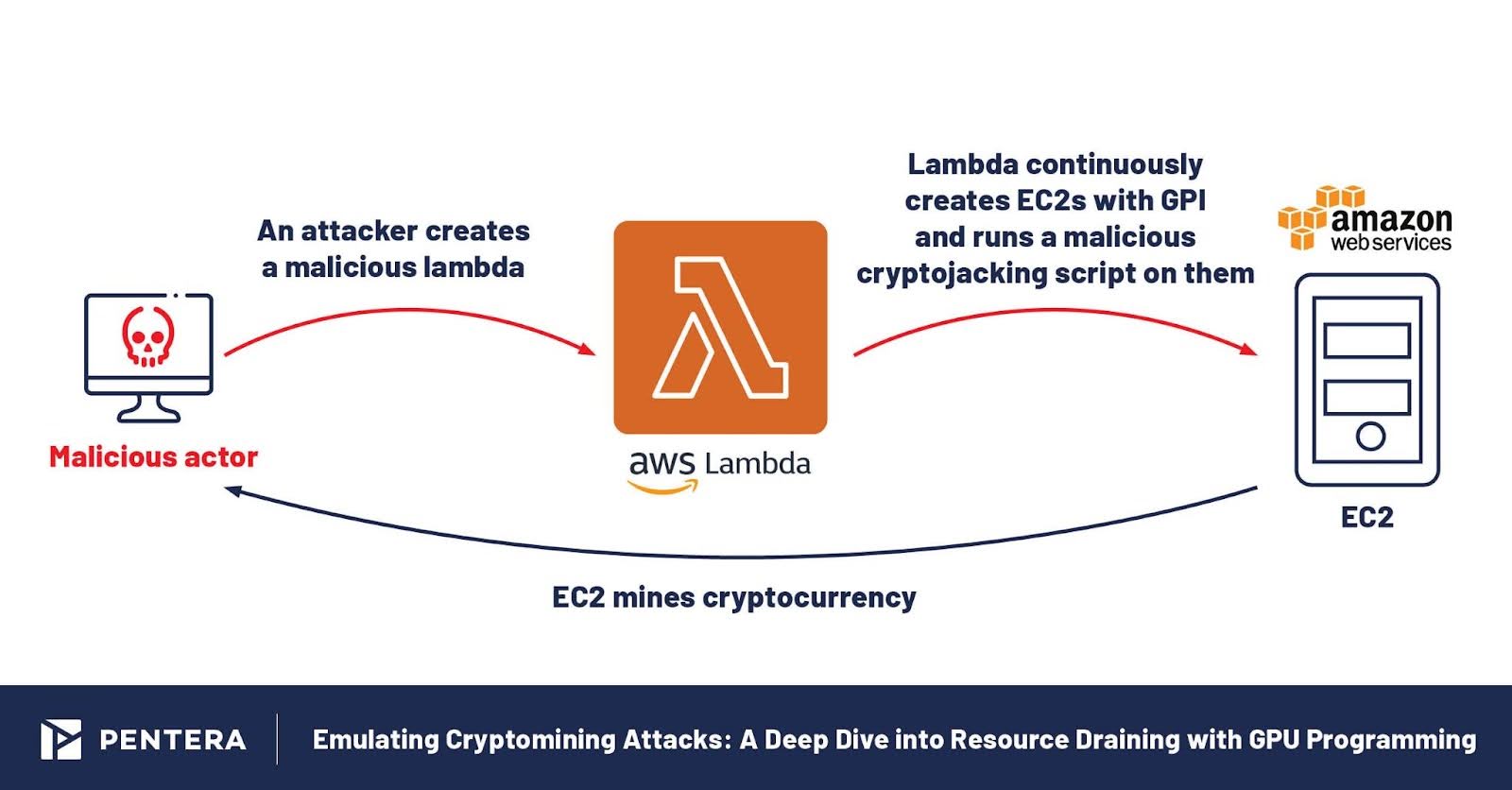
Diagrams showing cryptomining attack chains on cloud/GPU systems.
Espionage: Stealthy Side-Channel Leaks via GPU Drivers and Architecture
For nation-state or corporate spies, GPUs offer covert channels to infer secrets without direct access.
Key Methods:
- Side-Channel Attacks: GPUs leak timing, power, or contention data.
- GPU.zip (2023): Exploits undocumented data compression in iGPUs (AMD, Intel, Apple, etc.) to steal pixels from web pages, even cross-origin—revealing passwords or sensitive visuals via SVG filters.
- Multi-GPU Contention: In shared systems (e.g., NVIDIA DGX/NVLink), attackers monitor interconnect congestion for covert channels (up to 4 MB/s bandwidth) or fingerprint applications (e.g., identifying ML models or HPC workloads running on remote GPUs).
- NVBleed (2025): Targets NVIDIA multi-GPU links for high-bandwidth covert communication and profiling deep learning apps.
- Driver-Based Spying: Vulnerabilities allow malware to hide in GPU memory (e.g., Jellyfish PoC or sold toolkits executing code directly on GPU, bypassing CPU scanners). User-mode counters in GPUs can be abused for system spying.
- Real-World Impact: In cloud/HPC environments, a co-located malicious tenant spies on victims via shared GPU resources—leaking training data, keystrokes, or even 3D rendering secrets.

Visual of bitcoin mining process, analogous to illicit GPU exploitation.
Why GPUs Are Vulnerable
- Drivers run with high privileges (kernel mode) but have a large attack surface.
- Shared resources in multi-tenant setups (clouds, HPC) enable contention leaks.
- Undocumented features (e.g., compression) create unintended channels.
- Mining demand historically drove exploits (e.g., 2022 LAPSUS$ NVIDIA breach leaking driver code).
Protection Tips
- Update Drivers: Always install official patches from NVIDIA/AMD/Intel—2025 bulletins fixed dozens of critical flaws.
- Monitor Usage: Watch for unexplained GPU load (tools like Task Manager or GPU-Z).
- Security Software: Use endpoint protection detecting cryptojacking; disable unnecessary WebGL/JavaScript.
- Best Practices: Avoid pirated software, restrict management interfaces, use virtualization isolation in multi-GPU setups.
- For Enterprises: Segment GPU resources, monitor for anomalies in clouds.
GPU exploits blend profitability (mining) with stealth (espionage), evolving rapidly. Stay vigilant—your graphics card could be working for someone else!
