Device drivers—especially kernel-mode drivers—are a favorite target for hackers because exploiting them grants far greater power than compromising regular user-mode applications. While app vulnerabilities might allow control over a single program (e.g., stealing data from a browser), driver exploits often lead to full system compromise. Here's why attackers prioritize them in 2025.
1. Kernel Privileges: The Ultimate Power Grab
Drivers typically run in kernel mode (Ring 0), the highest privilege level in operating systems like Windows and Linux. This gives direct access to hardware, memory, and core OS functions.
- Exploiting a driver vulnerability allows privilege escalation from user mode to kernel mode, bypassing all restrictions.
- Once in kernel mode, attackers can:
- Disable antivirus/EDR tools.
- Hide processes, files, or network activity.
- Install persistent rootkits that survive reboots.
- Manipulate firmware or steal sensitive data at the hardware level.
In contrast, user-mode app exploits are sandboxed—crashing or controlling one app doesn't affect the entire system.
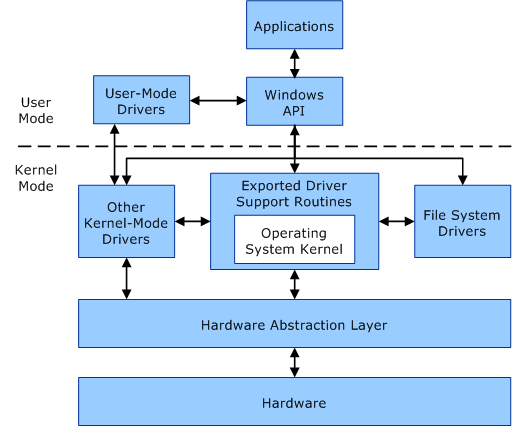
2. Evasion and Stealth: Harder to Detect
- Many security tools (AV, EDR) rely on kernel components themselves. A kernel exploit can disable or corrupt these defenses without triggering alerts.
- Techniques like Bring Your Own Vulnerable Driver (BYOVD) are rampant: Attackers load a legitimate but vulnerable signed driver (e.g., from old hardware vendors) to execute malicious code in kernel space, evading signature checks.
- Kernel exploits enable advanced persistence, like hooking system calls or modifying MSRs (Model Specific Registers).
App exploits are more visible—user-mode hooks or injections are often caught by behavioral monitoring.



Illustrations of privilege escalation paths via driver flaws.
3. Larger Attack Surface and Real-World Impact
- Drivers have a huge codebase with complex interactions (e.g., IOCTL handlers for hardware communication), leading to frequent bugs like buffer overflows or use-after-free.
- Recent 2025 examples:
- CVE-2025-62221: Actively exploited use-after-free in Windows Cloud Files Mini Filter Driver for privilege escalation.
- Lenovo driver flaws (CVE-2025-8061) abused in BYOVD attacks.
- Ongoing campaigns exploiting legacy drivers for EDR killing and ransomware deployment.
These enable ransomware (e.g., terminating protected processes) or espionage (e.g., persistent access in APTs).


Visuals depicting hackers exploiting driver vulnerabilities.
Trade-offs for Attackers
Drivers are harder to exploit reliably (e.g., blue screens on failure) and require initial access (often admin privileges for BYOVD). But the payoff—god-mode access—makes them worth it for advanced threats like nation-states or ransomware gangs.
In summary, drivers are the "keys to the kingdom." Microsoft and others block known vulnerable drivers via blocklists, but new ones emerge constantly. Keep systems patched, enable HVCI (Hypervisor-protected Code Integrity), and restrict driver loading for better defense!
